Understanding BYOD policy enforcement and creation
A well-defined BYOD policy is critical for any organization that allows consumer devices on the network. Communicating and enforcing the BYOD policy can prevent many problems.
Allowing employees to use their personal mobile devices for work-related tasks can provide plenty of advantages, such as quicker connectivity to business resources and reduced hardware costs, but the risks include security vulnerabilities, support costs and potential liability issues.
Organizations that allow employees to bring personal devices to work should have a well-defined BYOD policy and mechanisms to enforce it.
Defining a BYOD policy
The first step in creating a BYOD policy is defining the scope of control that the organization expects to maintain over employee-owned devices. Organizations could take plenty of different approaches here. On one extreme, an organization could treat personal devices like corporate assets in return for allowing employees access to IT resources from those devices. The other extreme is to assume no control over the devices themselves and instead focus on access controls and limiting risks such as leaving corporate data on BYOD devices. The optimal BYOD policy may lie somewhere between these two limits.
A BYOD policy should address acceptable use of corporate IT resources on mobile devices, minimal security controls on the device, the need for company-provided components, such as Secure Sockets Layer (SSL) certificates for device authentication and user identity, and the rights of the business to alter the device. The most common way this manifests itself is how IT departments handle lost or stolen devices.
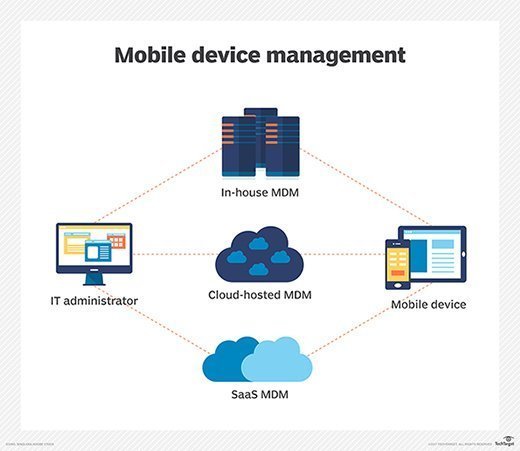
Acceptable-use policies could require a VPN when accessing corporate systems and prohibit the storage of passwords to business applications. Security controls might also require encryption for stored data, device password protection and registration of devices with a mobile device management (MDM) platform or a more comprehensive platform such as unified endpoint management (UEM), which includes MDM capabilities. IT administrators should ensure that employees understand all aspects of the BYOD policy and consent to them.
However, written policies and employee consent are not enough to protect an organization's information assets. Even well-intentioned employees can make mistakes, such as forgetting to set a device password or downloading confidential information over an unencrypted session. Mobile device policies should have an enforcement mechanism to ensure that these policies prevent such actions.
Enforcing a BYOD policy
Chances are that an organization's existing applications can enforce a BYOD policy, including Microsoft's Office 365 or Microsoft 365 subscriptions. However, before an IT department uses these apps, it should consider the following key questions:
- Are these applications sufficient to meet all security requirements?
- How difficult is it to manage mobile devices with these applications?
Organizations should consider if any of their existing licensing investments will give them the tools they need for device management.
Microsoft's Azure Active Directory (AD) and Office 365 subscription plans provide app-based protection and policy enforcement, including data loss prevention controls such as removing copy and paste functions and restrictions on application data sharing. However, this does not provide full device-level management. Additionally, organizations that employ Microsoft Azure AD and Microsoft's multifactor authentication can provide an additional layer of security to prevent users from authenticating against corporate applications -- unless a device meets specific requirements such as MDM enrollment. If these enforcement mechanisms are sufficient for an organization and the employees use supported devices, Microsoft Office 365 app-level protections could address all of its BYOD policy needs.
Third-party MDM platforms can support a wider array of BYOD policy enforcement operations, including full lifecycle management, app inventory control, data protection, certificate distribution, device configuration and lockdown.
BYOD policy enforcement begins with provisioning. MDM platforms can ensure consistent device configuration, install applications and create accounts on self-service management portals. If existing policies limit the apps that IT can deploy to a BYOD device, the IT department can use an MDM system that accounts for unauthorized app detection.
Most MDM applications support remote wiping, but completely wiping a device is drastic and, in many cases, may not be necessary. MDM apps can selectively wipe data, allowing device administrators to delete corporate data while leaving personal data intact.
A BYOD policy may also require that all devices accessing corporate systems be registered with the IT department and configured with an SSL certificate for authentication. MDMs that support certificate distribution can minimize management headaches for this operation. MDM systems can further ease that burden by reporting on expired certificates, revoked certificates and other certificate management concerns.
MDM systems also allow IT admins to recommend, and in some cases enforce, device OS updates and patches. While forcing an OS update on an end user's personal device may walk the line between privacy and security, ensuring that devices accessing corporate data are on a minimum OS or patch level may be required to provide a strong security posture. MDM systems allow IT admins to create OS compliance policies, such as minimum OS versions, for devices to enroll and be granted continued access to corporate applications.
Finally, look for MDM platforms for device configuration and lockdown functions. IT may want to lock down cameras, Bluetooth, GPS and Wi-Fi for some users. If the mobile admins specify an encryption policy, look for an MDM that can enforce this policy.
There are also new BYOD programs from the major mobile OS distributors with Apple's User Enrollment and Google's Android Enterprise Work Profile. These programs are new enrollment methods that allow IT to maintain and secure corporate applications and data while still restricting how much administrators can see within the MDM platform. These programs marry privacy and security to give IT admins and users what they might need.
A quality BYOD policy has two main characteristics: clearly defined policies and a consistent enforcement mechanism. A BYOD policy should address acceptable use, security controls and the business's rights to alter the device. Existing enterprise applications, such as Microsoft Exchange ActiveSync and certificate management systems, may be sufficient to enforce policies. If an organization requires more control over devices and the ability to generate management reports about BYOD use, a full MDM platform may be a better option.
What devices are acceptable for BYOD management?
Having a BYOD policy is important, but it's just as important to have a strategy for the type of devices that IT allows within that policy. Not all devices are created equal.
End users have a lot of choices regarding the type of device they want to use, which also means that IT cannot control an important security layer: the device's software and security update level. It also can't determine for sure if that device will see update support down the road. An MDM system can retain some control by allowing IT to create compliance policies around minimum software versions for device enrollment and application access.
IT administrators can also give end users a recommended device list for Apple and Android devices. Apple devices tend to be less difficult to recommend as they are well supported by Apple, but target devices that Apple still supports with the latest OS build. Google has its Android Enterprise Recommended website where admins can view devices that Google considers good options in a business setting for Android users. Google verifies devices on this list to meet strict requirements for hardware and software, including minimum OS update and patch support for at least three years. Each device on this list is verified to support proper management and enrollment from an MDM.
These policies can be frustrating for end users with devices that do not meet the minimum requirements for OS version or other criteria. IT can often help these users through steps such as validating if their device runs the latest OS, and there may be other avenues to get their device to a compliant state. However, users may need to either upgrade their personal device -- perhaps with a subsidy from their organization -- or enroll in a corporate-owned device program.





