mobile data
What is mobile data?
Mobile data is internet content delivered to mobile devices such as smartphones and tablets over a wireless cellular connection. Mobile data plans offer varying amounts of data transfer per month for a range of rates.
When users email, access webpages or use mobile apps, their devices receive and transmit data from the internet. In the absence of a local Wi-Fi connection, a mobile device usually connects via a subscription service with a cellular network provider. Consumers and business users often think of the meaning of mobile data in terms of cost and usage because mobile data is measured separately from voice calls and can increase monthly bills.
The increase in mobile users and the number of devices they own, as well as popularity of high-bandwidth applications such as streaming video and video conferencing, is causing the amount of mobile data consumed every year to climb. Telecommunications company Ericsson's annual Mobility Report, published in June 2021, estimated the monthly amount of global mobile data traffic at 49 exabytes. The report predicted that number will exceed 237 exabytes per month in 2026.
Mobile data vs. Wi-Fi
A mobile data plan and a Wi-Fi connection both enable a user to access internet resources without a wired connection. Wi-Fi refers to a wireless local area network, which has a limited range. When a user connects to Wi-Fi, their device accesses a wireless router or access point covering a specific area.
A mobile data connection enables a user to access the same internet resources over a cellular network owned by a telecommunications provider such as Verizon or AT&T. In this case, the mobile device connects to a cell tower that is part of a network spanning a very large geographic area. While this access offers convenience and flexibility, it comes with a cost per gigabyte of data transfer according to the terms and policies of the user's cellular plan.
How does mobile data work?
Mobile data creates a wireless connection by enabling devices to communicate through radio frequencies. The data uploaded or downloaded via a mobile network is broadcasted from or to a central cellular base station or macrocell, often housed on a cell tower. A single macrocell can cover a broad geographical location, and multiple cells can overlap to transmit data effectively and ensure coverage across thousands of miles.
Cellular providers have offered mobile data through a number of different technologies incorporated into a progression of mobile networks identified by "generation." The history of mobile data networks include the following:
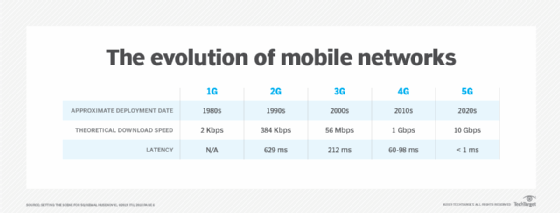
First generation or 1G
1G transmitted voice over cellular networks using analog telecommunications standards first introduced in 1979 and into the 1980s. 1G networks did not transmit mobile data.
Second generation or 2G
2G introduced digital voice in the early 1990s, ushering in widespread data communications. Most 2G networks used Global System for Mobile communication (GSM) based on Code-Division Multiple Access (CDMA) for transmission, but as technology evolved, General Packet Radio Services and Enhanced Data Rates for GSM Evolution were also adopted. 2G technology allowed mobile providers to begin offering text messaging and multimedia transmission using Short Message Service and Multimedia Messaging Service.
Third generation or 3G
3G networks, first deployed in the early 2000s, offered much higher speeds and bandwidth than previous generations. Based on the CDMA2000 family of standards, 3G implemented Universal Mobile Telecommunications Service and high speed packet access for better performance. These technologies were able to support video calling and the diverse applications that modern smartphones made popular.
Fourth generation or 4G LTE
In the 2010s, 4G replaced 3G as the newest iteration of cellular technology. 4G transmission used Multiple Input Multiple Output and orthogonal frequency-division multiplexing technologies. Some networks were called "4G LTE" because they incorporated Long-Term Evolution (LTE), a technology developed to help ease the transition from 3G to 4G. 4G network advantages included improved cell density, voice over IP capabilities and bandwidth.
Fifth generation or 5G
5G refers to cellular network technology being rolled out in the 2020s. These networks are built on a foundation of 4G LTE but use a system of small cell stations (rather than large cell towers) to support the explosion of connected devices and expand coverage and speed. Other benefits of 5G include low latency and real-time communication capabilities. Researchers are also working on 6G network technology, which will facilitate the growth of edge computing and the internet of things.
Mobile data usage today
Upgrades to 5G networks will increase the overall availability and transmission rates of mobile data. 5G-enabled laptops and tablets will also be able to connect directly to the cellular network, removing the need for a Wi-Fi connection. So the amount of data an individual might use could increase drastically. The cost of that data is continuing to rise, making it important for consumers to understand their usage and manage it where appropriate.
Many everyday activities and apps use large amounts of mobile data, and devices and apps can burn data in the background when they are not even in use. Consumers actively access mobile data when they browse the internet, listen to a podcast or read email. The amount of data expended for common activities is listed in the table below.
| Activity | Data requirement |
| 50 KB per message | |
| Uploading pictures | 1.5 MB per photo (variable) |
| 1-2 MB per minute (autoplay video disabled) | |
| Web surfing | 2.5 MB per minute (variable) |
| Gaming | 1.5 MB per minute (highly variable, applies only to gaming online) |
| Music streaming | 1-2 MB per minute |
| Podcast streaming | 60-100 MB per hour, depending on buffering and data quality, and compression |
| YouTube | 2.5-6 MB per minute, higher end for high definition (HD) video |
| Netflix | 1 GB-3 GB per hour, higher end for HD |
How to manage mobile data usage
Some mobile data plans offer unlimited data, but others strictly limit the amount that can be used. Data caps specify the maximum amount of data a user can access within a billing period. As a rule, when the user exceeds that limit, they are charged at a higher rate for additional data use. In other cases, a mobile provider may not charge overage fees, but instead throttle, or restrict, a user to a slower tier of service as they are approaching or after they meet the cap.
There are several ways users can monitor how much data they use and proactively manage it, depending on the brand of their device and telecommunications provider.
How to manage data usage through a mobile network provider
By accessing their account online or calling customer service, a mobile user can check data balances. Many providers proactively notify users to help them stay within consumption limits. Some also allow customers to send alerts when usage reaches a certain number or to begin using data saving options as they get close their data cap.
How to manage mobile data usage on iOS devices
IPhone and iPad users can go to Settings on their devices to manage mobile data, according to Apple. By selecting Mobile Data or Cellular Data, they can view the total amount of data used, as well how much each app has consumed. Users can conserve data by disabling cellular data access for specific apps. The apps will still work, but only when they are able to access a Wi-Fi network. Third-party applications such as DataMan and My Data Manager also allow users to track data usage in real time.
How to manage mobile data usage on Android devices
While Android devices do not have app-specific data settings similar to iOS, Android provides users the option to limit or stop usage. According to Google, users can navigate to Settings > Network & internet > Data usage. Under "Mobile," they can view total mobile data used, set alerts and automatically turn off mobile data at a certain threshold. The Google Play Store also offers Android users several options for third-party apps to monitor usage. These include Datally and GlassWire.
IT and business leaders may manage mobile data on employee devices, but they are generally most interested in ensuring security and data protection. Learn about these issues in "The ultimate guide to mobile device security in the workplace."