
What is the consumerization of IT (IT consumerization)?
The consumerization of IT refers to how software and hardware products designed for personal use have migrated into the enterprise and are used for work purposes. The influx of user-friendly consumer devices, applications and platforms into enterprises has fundamentally changed how work gets done and how corporate IT services are provisioned for use in enterprise workflows.
As far back as 2005, enterprise advisory firm Gartner anticipated that most new enterprise technologies would originate from consumer applications. Twenty-five years later, Gartner has been proven right, and IT consumerization continues to drive workplace innovation from the bottom up.
The consumerization of IT has accelerated with the rise of remote work, mobile computing and cloud-based productivity tools. It reflects the way the lines between work and home have blurred and underscores the powerful impact of user-friendly consumer technologies on the business world.
The term consumerization of IT was coined in 2001 by Douglas Neal and John Taylor of the British research and advisory organization Leading Edge Forum. Neal and Taylor anticipated that consumer technologies would improve faster than enterprise technologies because there are more consumers than IT users.
This article is part of
The evolving CIO role: From IT operator to business strategist
How does IT consumerization work?
IT consumerization works through a bottom-up adoption process that's driven by employees' familiarity and preference for the technologies they use in their personal lives. Workers are increasingly bringing the computing devices and apps they use at home into the workplace because they are familiar and often more user-friendly than traditional enterprise systems. This grassroots adoption often precedes formal IT approval and, in many cases, influences enterprise purchasing decisions when IT eventually formalizes support for these tools.
In many ways, the IT consumerization trend can be traced to the dot-com collapse of the late 1990s and early 2000s. At this time, enterprise IT budgets shrank and IT vendors shifted their focus to the consumer market in response. Today, new IT innovations often enter the consumer market first before moving into the enterprise market. This is a reversal of the historical pattern in which technology was typically developed for business or government use and later adapted for consumers.
What is an example of IT consumerization?
Apple's iPhone is a popular consumer product that exemplifies the concept of IT consumerization. Within a few years after its introduction in 2007, employees were using the feature-rich smartphone for work-related tasks, such as checking email, managing calendars and accessing documents.
The blending of personal and work technology in the early days of smartphones marked a sharp departure from the pre-consumerization era, when chief information officers decided what technology employees could use for work and corporate IT departments were responsible for managing it.
This user-driven shift challenged the dominance of enterprise-issued devices, such as BlackBerry smartphones, which had been the standard for secure corporate communication. Over time, as employee demand grew, many companies were forced to adapt by implementing bring your own device (BYOD) policies and updating their mobile device management strategies to accommodate iPhones and other consumer devices.
Other examples of the consumerization of IT
Here are some other examples of consumer-type IT commonly deployed in the workplace:
- Marketers use consumer-oriented social media websites such as Facebook, Instagram, LinkedIn or X (formerly Twitter) for enterprise publicity, brand-building, audience outreach and customer engagement.
- Cloud services, such as Gmail or Dropbox, were originally designed for individual users but quickly gained popularity in business environments.
- Video conferencing services, such as Zoom, Microsoft Teams and Google Meet, began as consumer-friendly platforms suitable for small and medium-sized businesses as well. They have since become essential business tools for internal collaboration, remote work and external meetings.
- Virtual reality and augmented reality platforms are now being used for virtual meetings, corporate training, product development, product testing, marketing, product virtual tours and recruitment.
- ChatGPT and Google Gemini, formerly Bard, were released to consumers first. Employees quickly saw the value of the generative AI chatbots in the workplace.
What is the impact of IT consumerization?
The adoption of consumer technology in the enterprise has compelled IT departments to adapt their management strategies to support a broader range of devices, platforms and cloud services. This shift reflects more than just a change in tools; it represents a broader cultural transformation in how technology decisions are made and how new products are introduced across the organization.
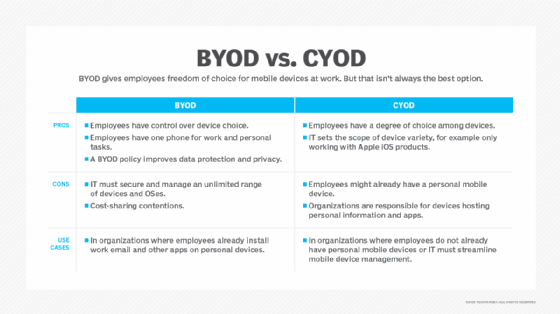
Allowing employees to choose and use the technologies they prefer can enhance productivity, streamline workflows and improve the overall workplace experience. In response, many organizations have taken deliberate steps to accommodate personal technology use by implementing BYOD or choose your own device (CYOD) policies and becoming more flexible about the use of cloud-based productivity applications. These changes reflect a growing recognition that user-centric IT can drive both higher engagement and greater operational efficiency.
The consumerization of IT has also changed the way vendors are rolling out their software products. For example, OpenAI launched ChatGPT publicly in November 2022 as a free, consumer-facing chatbot. Its widespread popularity led to the development of business-grade versions, such as ChatGPT Enterprise, and application programming interface integrations for developers and companies.
Similarly, Google Gemini was initially made available to consumers before Google began integrating it into its Workspace suite, cloud services and enterprise-specific tools. This rollout strategy reflects a broader trend in IT consumerization: Consumer adoption often drives enterprise interest and shapes product evolution.
Drivers of the consumerization of IT
IT consumerization and democratization have been largely driven by the widespread popularity of mobile devices, the ubiquity of high-speed broadband internet and an increasing number of high-quality software-as-a-service applications. Cloud-based apps have made it easier than ever for employees to access powerful digital tools outside traditional IT channels. In turn, this has fundamentally reshaped the way technology is introduced and used in the workplace.
One of the most significant drivers of consumerization is the design philosophy behind personal technology. Unlike many enterprise tools, consumer apps and devices are built to be intuitive, visually appealing and easy to use. These are qualities that resonate strongly with employees who want technology that doesn't require extensive training or support.
Another factor driving IT consumerization is that consumer software can often be purchased online and used immediately. This can empower workers who want to bypass corporate IT procurement processes. One important result of this empowerment is that product selection criteria for corporate-owned devices and software have expanded beyond cost and technical features. Today, these criteria often include employee preferences because tools that employees find enjoyable to use are more likely to be adopted quickly, used effectively and deliver a higher return on investment.
Frustration with the slow pace of innovation in traditional business technology has also contributed to the shift toward consumerization. Employees, particularly those in fast-moving industries or tech-savvy roles, might often find themselves limited by outdated software. As a result, they might turn to consumer-grade alternatives that offer more features and a better digital experience.
The changing workforce demographic is driving IT consumerization as well. Younger employees are less inclined to draw a firm line between personal and professional technology. These digital-native employees have grown up with smartphones, cloud apps and on-demand services, and they tend to expect similar levels of convenience, mobility and usability in their workplace technology.
What are the benefits of the consumerization of IT?
IT consumerization is not a strategy or tactic that can be adopted. Rather, it is an idea that reflects how organizations can benefit from devices and technologies that originated in the consumer space. There are numerous advantages of the consumerization of IT, including the following:
- Reduced cost. The use of personal tech shifts the capital expenses of smartphones and other hardware to employees.
- Improved employee satisfaction. Workers are more engaged and comfortable using tools they already know and like.
- Increased productivity. Familiar technology reduces training time and can accelerate tool adoption.
- Greater flexibility for employees. Employees can work from anywhere using personal devices and cloud-based applications.
- Faster innovation. Business divisions and teams can use cloud apps to meet an immediate or temporary need.
- Enhanced talent attraction and retention. Having the ability to use personal tech can help attract and retain digital natives.
- Reduced time to value. Software tools that employees already know how to use can enable businesses to realize their benefits faster.
- Streamlined workflows. Employees can streamline workflows across their own mobile devices, computers and tablets to ensure workflow continuity and little or no time wasted in application/device switching.
What are some challenges of the consumerization of IT?
The consumerization of IT brings several challenges for enterprises, especially in areas related to security, support and governance. Here are some of the most significant challenges:
- Data security risks. Personal devices and unvetted apps might lack enterprise-grade security controls and increase the risk of data breaches or leaks.
- Compliance and regulatory issues. Consumer apps might not meet industry-specific data-handling requirements, potentially exposing the organization to legal or regulatory penalties.
- Device and application management complexity. Supporting data access for a wide range of personal devices and third-party apps increases the burden on IT teams.
- Inconsistent user experiences. Multiple operating systems and platforms can lead to compatibility issues and fragmented workflows.
- Support and troubleshooting challenges. IT teams might struggle to troubleshoot IT problems because of the greater variability in devices and apps.
- Employee burnout. When employees use their own technology for work, it can make it easier to maintain a work-life balance.
How is IT consumerization related to BYOD?
When a business implements a BYOD policy that allows employees to use their own computers, smartphones or tablets for work, IT teams need to implement safeguards that ensure those personal devices won't pose a risk to the organization.
One approach is to deploy unified endpoint management (UEM) tools. UEM platforms integrate capabilities that were once handled separately by mobile device management, mobile application management and traditional desktop management tools. They enable IT to manage laptops, mobile devices and mobile apps from a single console and ensure that BYOD policies are uniformly and consistently enforced throughout the organization.
To further protect sensitive information, some enterprises use application containerization or sandboxing to prevent users from storing corporate data locally. Secure access controls, such as two-factor authentication and device hygiene checks, can add another layer of protection. A hygiene check is an access control that verifies a personal device meets specific security and policy requirements before it is allowed to access the corporate network.
Together, these measures help organizations balance the flexibility of BYOD with the security and governance required in a professional IT environment.
How are companies implementing BYOD policies?
BYOD policies can take different forms, depending on an organization's size, goals, industry regulations, risk tolerance and workforce needs.
Large enterprises have traditionally leaned toward establishing strict, IT-managed BYOD frameworks. They might mandate device enrollment within the corporate network, require remote wiping capabilities in case of loss or theft and impose specific restrictions on device usage to safeguard sensitive company data.
In contrast, smaller businesses might adopt a more lenient stance that enforces BYOD requirements through an acceptable use policy (AUP). For example, the AUP might require that employee-owned devices need to meet fundamental security hygiene requirements, such as having antivirus software installed, before the device can be granted access to the corporate network.
The scope of application access that's granted under a BYOD policy can also vary significantly. Some organizations limit the use of personal devices to basic functions, such as email and calendar access, while others maintain an allowlist of apps their employees can use. If a company is cloud-first, it might even support full access to enterprise applications and corporate data because its IT team will be able to centrally manage user access, permissions and data security across all cloud applications.
IT consumerization and shadow IT
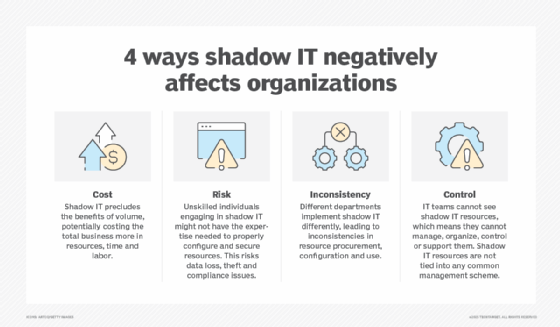
Outside of cloud environments, the trend toward IT consumerization has created challenges that have been historically associated with shadow IT. Shadow IT refers to the implementation of technology by employees without the knowledge, explicit approval or governance of the IT department.
As employees grow accustomed to intuitive, user-friendly consumer apps, many will download and use unapproved tools that help them get work done faster. The problem is that, without IT oversight, these tools might lack proper encryption, fail to meet data residency requirements or store sensitive information outside of approved environments.
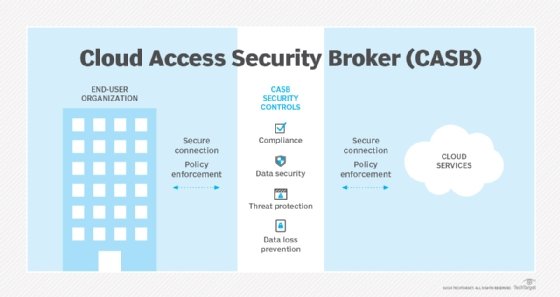
The loss of visibility and control increases the risk of data exposure, intellectual property theft and compliance violations. To mitigate this risk, many organizations use application discovery and network traffic analysis tools as well as cloud access security brokers to make it safer for employees to use their own devices for work.
Best practices for managing BYOD and reducing shadow IT risks
To successfully support a BYOD environment while minimizing the risks associated with shadow IT, organizations must adopt a multilayered strategy that also supports an organization's broader goals of digital transformation, mobility and workforce empowerment. Here are some best practices for managing BYOD that can help IT teams strike the right balance between flexibility and security:
- Develop and enforce a clear BYOD policy. A well-defined BYOD policy should outline who is eligible to use personal devices, what devices are permitted, what data can be accessed and what security requirements must be met.
- Deploy unified endpoint management software. A UEM platform enables IT to centrally manage corporate and personal devices from a single console. Most UEM tools support role-based permissions that allow for differentiated access levels based on job function or device risk.
- Implement application allowlisting. Limiting access to a curated list of approved apps can help prevent the use of risky or noncompliant tools.
- Monitor for shadow IT activity. Use tools that can discover and monitor unauthorized applications or services being used on the network.
- Educate and engage employees. Provide ongoing training that explains the risks of using unapproved apps, the value of data protection and the benefits of using officially supported tools.
- Adopt a cloud-first or zero-trust architecture. Cloud-first principles and zero-trust security models can make BYOD less risky because they can help ensure that only authorized users on compliant devices can access sensitive resources.
- Control access to enterprise apps. Consider providing employee access to enterprise apps only through IT-controlled virtual desktop infrastructure or desktop as a service.
The future of IT consumerization
In the early years of mobile computing, some advisory firms reported how the loss of centralized governance and purchasing consolidation drove costs up and diminished productivity. At the same time, tech vendors such as Cisco were reporting that IT consumerization, specifically BYOD, could actually increase organizational productivity and lower costs.
Today, the adoption of consumer IT in the enterprise is not an option -- it's a given. As a result, IT departments need to develop management strategies that prioritize employee experience as a core IT and human resource objective.
Expect the future of IT consumerization to be defined by a continued shift toward BYOD and employee-driven technology adoption. As digital-native employees raise the bar for usability and mobility, organizations will need to deliver consumer-grade experiences while maintaining strong security, data governance and compliance controls.
The payoff can be significant. When organizations embrace this aspect of digital transformation, they can turn IT consumerization into a strategic advantage that enhances productivity and improves employee satisfaction.
Now that you know more about the consumerization of IT, it's time to learn how to lead a successful digital transformation from the bottom up.





