
mobile application management (MAM)
What is mobile application management?
Mobile application management (MAM) is software that secures and enables IT control over enterprise applications on end users' corporate and personal smartphones and tablets.
MAM software allows IT administrators to apply and enforce corporate policies on mobile apps and limit the sharing of corporate data among apps. It also enables the separation of business apps and data from personal content on the same device. Other common MAM features and capabilities include software delivery (often through an enterprise app store), software license management, app configuration, inventory management and application lifecycle management.
Why mobile application management is important
Mobile application management provides IT administrators with a more granular way to control and secure corporate data, which is important in any mobile strategy, particularly in bring your own device (BYOD) programs.
Traditionally, IT departments relied on mobile device management (MDM) software, which provides device activation, enrollment and provisioning capabilities, remote wipe and other device-level functionality. This approach sufficed for scenarios where an organization purchased mobile devices for employees who used them only for work-related matters.
But after Apple released the iPhone in 2007, followed by the release of Google Android-powered smartphones, more employees began using their personal devices for work. Many of these employees were reluctant to allow their IT departments to remote wipe their personal devices, blocklist certain apps or use other MDM capabilities. And as the workforce grew more tech-savvy, it became more difficult for organizations to completely block end users from doing work on personal devices. In addition, putting corporate data on personal phones was difficult to secure. As such, these devices and applications went unsecured, which created an enterprise risk.
MAM emerged to help solve this problem. As part of a larger mobile strategy, it allows IT administrators to apply and enforce policies only on specified apps that access corporate data, leaving personal apps and data untouched. Some of MAM's functionality is similar to MDM. With MAM, IT can remote wipe an app -- but not the whole device, as is the case with an MDM-managed device, for example.
How MAM works
There are several different approaches to mobile application management, including the following:
Software development kits (SDKs) and application wrapping. These methods involve additional code being added to an app, either during the use of SDKs or after (app wrapping) the development process. This code connects the app to back-end MAM software, enabling IT administrators to apply and enforce policies on the app and take other measures to protect its data.
Containerization. This approach, also known as application sandboxing, isolates an app or group of apps from other apps on a device. Data within this isolated area, known as a container, cannot leave, and apps within the container cannot interact with those on the outside. An extreme example of containerization is dual persona technology, which creates two separate user interfaces -- one for work and one for personal use -- on the same device.
Device-level MAM. Another method is the ability to control and secure apps through the MDM protocols built into mobile operating systems. Apple's Managed Open In feature, introduced in iOS 7, allows IT to control how apps share data. For example, an admin can prevent a user from downloading a document from their corporate email app and uploading it to a personal cloud storage app. Google Android uses sandboxing to create a secure, managed work profile containing corporate apps and personal data. Samsung offers similar capabilities on its Android devices through its Knox technology.
The major drawback to app wrapping, MAM SDKs and third-party containerization is that they do not always work across all mobile apps, operating systems and devices. The wrapping and SDK approaches require access to an app's source code, which is not always available -- especially for apps in a public app store. And Apple does not allow developers to abstract apps from iOS as containerization and dual persona require.
In response to this challenge, a group of enterprise mobility management (EMM) vendors formed the AppConfig Community in 2016. AppConfig defines tools and best practices that provide an open approach to configuring and securing mobile apps. This benefits users with a better out-of-the-box experience and businesses with secure apps that are easy to integrate. These are seamless to existing MAM systems in the popular unified endpoint management (UEM) products of this community. Members of the AppConfig Community include BlackBerry, SAP, IBM, VMware, Jamf Software, MobileIron, SOTI, Cisco and Meraki.
MAM challenges
While MAM has made great strides, the main challenges today are that MAM product solutions will vary greatly in features and capability. The challenge for IT admins and managers is determining which MAM product to use for their organization's needs. Organizations should consider the following:
- Security. Mobile devices are spread across a broad footprint, making it easier for users to be vulnerable to phishing and malware attacks. Consider the following recommendations for MAM security solutions:
- Third-party integration. If your organization has a third-party directory service such as Active Directory, G Suite or AWS, an MAM product must integrate with that service.
- Mobile security policy. Configuring and managing security via global policies must be available and easily managed. This includes the ability to define and enforce custom rules and apply different rules to different classes of users.
- Define and apply app-layer security. The user should be required to use secure authentication to access company data via an app. This will help prevent storing company data on a personal device or sharing data with unauthorized apps or users.
- App containerization. Techniques can vary or may not exist at all. Microsoft's Intune, for example, uses Conditional Access policies rather than containerization. And Conditional Access is only available for Azure AD P1 and P2 licenses, which could affect a decision to use Intune.
- App catalog delivery. While app catalog management is available in all major products, the implementation can vary. For example, Google Play and Apple's App Store have default public app stores and a custom catalog.
- App volume license support. The right platform must be able to apply volume licensing and management for applications. While most major products provide this support, product versions may vary. For instance, ManageEngine's Endpoint Central has four editions, but only the Enterprise and UEM editions provide License Management.
- Mobile operating system platforms. MAM products vary greatly in the mobile systems they support. It's critical for an organization to factor in what types of mobile operating systems it needs to manage.
MAM vs. MDM, EMM and UEM
Mobile application management was available as a standalone product from several vendors in the early days of the BYOD era. As the market matured, however, major enterprise software companies acquired standalone MDM and MAM vendors and began bundling their products. This collection of technologies became known as EMM.
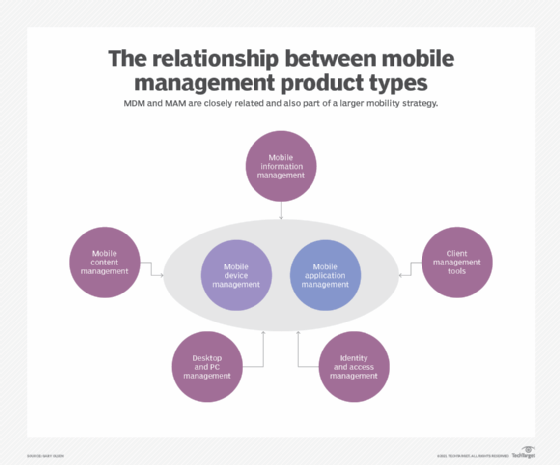
The main components of EMM are MDM, MAM and identity and access management. Some vendors also include enterprise file sync and share in their offerings. Although there was some MAM vs. MDM debate initially, it's common for organizations to rely on a combination of them to meet their security and IT administration requirements. An IT department may use MDM to enforce basic security measures, such as using a device passcode, and then rely on MAM for app protection to prevent data leakage from business apps, for example.
UEM evolved from EMM products because organizations needed a way to manage all their endpoints -- including desktops and laptops -- from one tool. Most UEM platforms can manage Windows and macOS devices, smartphones and tablets. Many existing EMM vendors combined their products with other tools to allow for hybrid management of desktops and mobile devices or added desktop management to their mobility management offerings.
Major vendors and products
Despite the abundance of UEM products available today, a few have risen to the top, including Microsoft, VMware, Ivanti and IBM. Others, such as BlackBerry, Citrix and MobileIron, remain popular alternatives. While less common, some vendors focus solely on MAM or enterprise app stores, including Digital.ai App Management, Appaloosa and App47.







