
mobile device management (MDM)
What is mobile device management?
Mobile device management (MDM) software allows IT administrators to control, secure and enforce policies on smartphones, tablets and other endpoints.
MDM is a core component of enterprise mobility management (EMM) and unified endpoint management (UEM), which aims to manage all endpoint devices with a single console. These platforms include mobile application management (MAM) tools, identity and access management, and enterprise file sync and share. The intent of MDM is to optimize the functionality and security of mobile devices within the enterprise while protecting the corporate network.
Modern enterprise mobility products support iOS and Android smartphones, tablets; Windows and macOS laptops, desktops; and even some internet of things (IoT) devices.
How mobile device management works
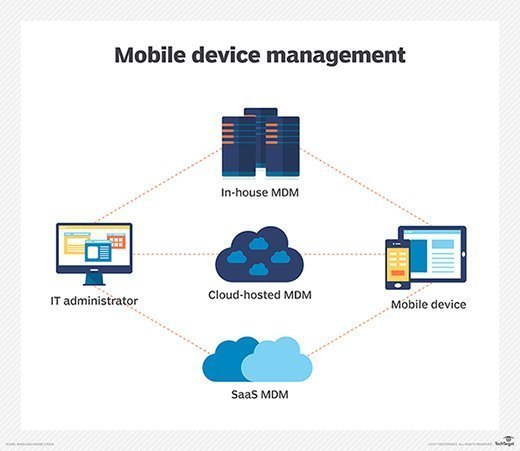
Mobile device management relies on endpoint software called an MDM agent and an MDM server that lives in the cloud.
IT administrators configure policies through the MDM server's management console, and the server then pushes those policies over the air to the MDM agent on the device. The agent applies the policies to the device by communicating with application programming interfaces (APIs) built directly into the device operating system.
Similarly, IT administrators can deploy applications to managed devices through the MDM server.
BYOD mobile device management
Mobile device management software emerged in the early 2000s to control and secure the personal digital assistants and smartphones that business workers began to use. The consumer smartphone boom that started with the launch of the Apple iPhone in 2007 led to the bring your own device (BYOD) trend, which fueled further interest in MDM.
Deploying MDM in a BYOD environment introduces some challenges. Organizations must balance IT's need to secure corporate apps and data with the end user's need to maintain privacy. Users are often concerned with IT's ability to monitor their actions on a mobile device, but privacy settings can help alleviate those concerns.
Organizations can use other methods to maintain user privacy while deploying MDM for BYOD environments. Some MDM platforms offer app wrapping, which provides a secure wrapper on mobile apps and enables IT to enforce strong security controls. For Android devices, organizations can use Android Enterprise, Google's enterprise mobility program that integrates with leading MDM platforms. Android Enterprise offers separate work and personal profiles so end users can keep their personal data away from IT's control, and IT admins can secure corporate data and apps as needed.
Mobile device management features
The developers of mobile operating systems and manufacturers of mobile devices control what MDM software can and can't do on their devices through their APIs. As a result, mobile device management has become a commodity, with most vendors offering a similar set of core capabilities. MDM vendor differentiation comes by integrating mobile device management servers with other enterprise software.
Common mobile device management features include the following:
- device enrollment for the onboarding of new devices and setting security policies;
- predefined user profiles set by your MDM administrator for quicker onboarding;
- device inventory and tracking with reporting throughout the entire mobile device lifecycle;
- self-service features that enable end users to resolve common IT issues, such as security updates, without having to put in a service desk ticket;
- app management, including distributing new apps, updating apps, removing unwanted apps or the use of an enterprise app store;
- integration with mobile threat defense (MTD) or mobile threat intelligence solutions to prevent malware and other attacks that target mobile devices;
- device hardware feature control enabling admins to restrict device camera usage and access to insecure public Wi-Fi networks;
- content management to govern and secure organizational content, such as sales enablement content on mobile devices;
- device location management via GPS and remote wipe to protect lost, stolen and otherwise compromised mobile devices;
- password enforcement that admins can manage through policies;
- reporting and analytics for tracking and reporting on device data and cellular usage, compliance and security;
- app allowlisting and blocklisting; and
- data encryption enforcement to help protect against malware and other data compromises.
7 best practices for mobile device management
- Develop a comprehensive mobile device policy as part of an overall cybersecurity strategy that outlines the organization's acceptable use of mobile devices, including device security, data protection and app usage guidelines. This policy should be regularly reviewed with IT, security and business stakeholders and regularly communicated to employees.
- Set usage policies as part of a comprehensive mobile device policy or as a standalone policy for corporate devices, starting with documented rules about data usage, roaming and international calling.
- Implement an MDM platform to manage and secure your corporate-owned and BYOD devices that will enable you to wipe lost or stolen devices remotely, monitor device usage, including cellular/data costs, and automate security updates and patches.
- Develop a secure configuration standard for corporate devices, including setting devices to receive security updates over the air (OTA). The device standard should also include strong passwords, encrypted storage for data security and automated device locking.
- Work with your mobile providers to choose the right corporate plan -- typically a shared data pool -- that offers your organization the most savings.
- Train employees on mobile device security, starting with best practices for securing their personal devices. The training should also cover the security of corporate-owned devices and the importance of securing corporate data, especially if the organization must meet industry compliance programs such as Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI-DSS) and Sarbanes-Oxley Act. The training must cover the consequences of noncompliance for the organization and the employee.
- Deliver BYOD-specific security training if the organization relies heavily on employees using their own devices to do their jobs. Such training should focus on how the organization protects corporate data on personal devices while not compromising the employee's personal data.
MDM vendor landscape
The MDM vendor landscape has changed significantly since its inception due to acquisitions of startups by larger firms seeking to add mobile device management functionality to their products and solutions portfolios.
Microsoft holds a dominant role in the market with its Enterprise Mobility Suite solution. Jamf has grown with its Jamf Pro product. A new generation of MDM startups, such as Esper, Fleet, Kandji, and Mosyle are jockeying for positions, especially with enterprises standardized on Apple devices. And device vendors like Apple are integrating MDM features into their device OSes.
SaaS is the current standard for MDM because of the increased flexibility and pay-as-you-go services model, making it easier for organizations to onboard and offboard devices. The pandemic and the rush to remote work showed that on-premises MDM systems are a relic of another age. SaaS-based MDM also offers potential customers a pilot or trial experience that's economical, dynamic and won't completely drain their internal IT staff on a one-off project.
The small and medium-sized business (SMB) market is a notable piece of the MDM landscape in 2023 compared to earlier years. Apple launched Apple Business Essentials in 2022 to help small businesses improve device management practices.





