BYOD (bring your own device)
What is BYOD?
BYOD (bring your own device) is a policy that enables employees in an organization to use their personally owned devices for work-related activities. Those activities include tasks such as accessing emails, connecting to the corporate network and accessing corporate apps and data. Smartphones are the most common mobile device an employee might take to work, but they also take their own tablets, laptops and USB drives into the workplace.
With more and more people working remotely and using personal devices, it's imperative for companies to execute and enforce BYOD policies. BYOD is not simply to eliminate the need for employees to carry two phones; a BYOD policy is designed to ensure that the employees use strong security practices when connecting to the company network.
While some organizations might endorse BYOD, others might see it as a facet of shadow IT, which indicates a hardware or software component that's not supported by the IT department.
How does a BYOD policy work?
A BYOD policy outlines what the company sees as an acceptable use of the technology, how to operate it and how to protect the company from cyberthreats such as ransomware, hacking and data breaches. It is critical to have a well-defined BYOD policy and understand the risks and benefits of BYOD in the organization.
The policy is generally available in a document that employees must agree to. It outlines that those employees needing to access corporate digital assets can use their personal devices if they meet the requirements defined within the BYOD policy.
A BYOD policy might include all or some of the following:
- Acceptable use. This policy defines what constitutes acceptable use of employee-owned devices for business activities.
- Approved devices. This defines the types of mobile devices approved for use by IT.
- Security measures. A BYOD security policy can entail certain measures such as password requirements. It can also include the software that must be installed to help with device security, for instance, mobile device management (MDM) or mobile application management (MAM) tools.
- Employee responsibility. This policy outlines user responsibilities around the device and its access to the network.
- Reimbursements. This policy might define any incentives or cost reimbursement to employees for using personal data plans for work-related activities
- Level of IT support. A company's BYOD policy might specify the level of assistance offered by its IT department in handling problems pertaining to broken or improperly functioning personal devices.
- Exit plan. An exit plan highlights what happens when an employee leaves or an employee no longer wishes to use their personal devices for work. It sets clear guidelines on how company data should be handled or removed from employees' devices and the decommissioning of user accounts.
What level of access does BYOD offer?
It is not uncommon to find that BYOD offers employees the same level of access to corporate resources as corporate-owned devices.
Exceptions include environments where the data is highly sensitive and under strict regulatory compliance requirements. In that case, IT would limit the level of access for employees using personal devices. These limitations might come up in government organizations, financial institutions that deal with sensitive data, or even top executives at an organization that might be the target of hackers. In those cases, IT departments might deploy corporate devices to help keep them more secure.
While the level of access can vary depending on an organization's policies and security requirements, general levels of access in a BYOD environment include the following:
- Level 1. This is the basic access level. Employees are usually permitted to use their personal devices to access basic company resources such as email and calendars at this level. Access to further company resources, though, can be limited.
- Level 2. This is also called controlled access. At this level, employees can use their personal devices to access a greater variety of company resources, such as data and applications. However, security measures are generally used to safeguard confidential data. A few examples of these controls include device encryption, secure authentication and data loss prevention techniques.
- Level 3. This is the full access level which grants employees complete access to all corporate resources -- including confidential data and apps -- on their own devices. However, there might not be a lot of safeguards in place, making it important for businesses to carefully weigh the advantages of BYOD versus the need to protect their data and resources.
What are the benefits of BYOD?
A well-controlled BYOD environment can bring many benefits to a business. Common benefits of BYOD include the following:
- Convenience. BYOD provides an important benefit to both companies and their employees. It creates significant convenience for employees as they no longer must carry multiple devices with them. It also enables them to choose the type of device they are most familiar with and comfortable using. BYOD policies also enable workers to work from anywhere, anytime.
- Cost reductions. For companies, BYOD means the IT department no longer has to purchase additional mobile phones for employees. This setup brings down their costs significantly and reduces some of the burden of supporting those mobile devices.
- Improved productivity. Employee productivity can potentially increase if they have the option to use familiar devices that are customized to their preferences. This familiarity and customization of BYOD devices can lead to faster task completion and improved overall performance.
- Latest technology. Employees frequently upgrade their personal devices more often than organizations update company-owned hardware. Permitting employees to utilize their own devices can enable organizations to access the latest technology without incurring additional expenses.
- Reduced training time. Employees who bring their own devices are already accustomed to using them. Thus, a BYOD policy can increase productivity by reducing the learning curve that comes with switching between operating systems, which can otherwise delay a new employee's onboarding process.
- Employee empowerment. BYOD might empower employees by letting them choose the devices and apps that work best for them. This can boost creativity, innovation and job satisfaction.
- Easier updates. Managing and updating laptops and work phones for all employees is time-consuming and expensive. However, if employees use their own smartphones and laptops, they are more inclined to stay current with software updates and replace hardware as needed, reducing the burden on the company.
What are the risks or challenges of BYOD?
While BYOD can bring numerous benefits to organizations, it also comes with its own set of challenges. Common challenges and risk factors of BYOD include the following:
- Complex support. IT support is straightforward when everyone uses identical work-issued devices. However, managing upgrades and maintenance can become more complex for the IT department when dealing with diverse individual pieces of equipment and operating systems.
- Limited IT control. IT generally cannot fully manage a BYOD device, because many employees might not want IT to have control over their personal data. Consequently, organizations might face challenges with enforcing security policies, updating software and guaranteeing uniform security measures across all devices. This issue makes it difficult for IT to ensure that hackers are not able to access these devices and deploy tools such as screen recorders or keyloggers.
- Increased security risks. With the rise in cybersecurity breaches, personal devices are becoming a huge target of cybercriminals. Also, personal computers might not be as secure as those owned by an organization, making them potential targets for threats including data breaches, malware infections, illegal access to sensitive information and loss of device or theft.
- Legal and compliance issues. BYOD policies can potentially give rise to compliance and legal issues, particularly in sectors where data protection and privacy requirements are stringent. Organizations must ensure that their BYOD policies comply with applicable laws and regulations.
- Employee privacy issues. When using their own devices for work purposes, employees might feel uneasy about the possibility of IT accessing their personal information and activities. They might also feel uncomfortable with installing IT-mandated software on their personal devices.
BYOD vs. corporate-owned policies
Besides BYOD, there are a few other models and corporate policies for device management.
The alternative models to BYOD include the following:
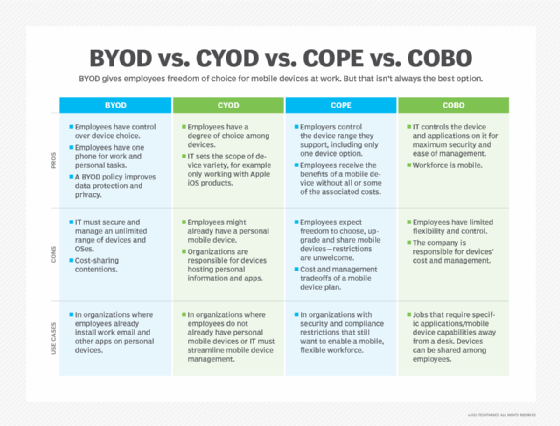
- Company-owned, business-only (COBO). The COBO model entails the organization acquiring and owning devices exclusively for business purposes. These devices are dedicated solely to work-related tasks, prohibiting personal use. COBO offers the utmost control and security, as the organization has complete control over the ownership and management of the devices.
- Choose your own device (CYOD). In the CYOD approach, the organization provides a selection of permitted devices from which employees can choose. The company retains ownership and control of the equipment, enabling standard management and security procedures. This model affords employees considerable flexibility while maintaining IT control and device management.
- Company-owned, personally-enabled (COPE). The COPE model requires the business to acquire and own the devices used by employees. The devices are customized to fulfill both business and personal demands, enabling employees to utilize them for both professional and personal purposes. COPE provides a combination of control and flexibility because the business might impose security standards while facilitating personal use.
These policies might affect employee satisfaction, however, because they require them to carry additional devices.
BYOD best practices
To successfully execute BYOD, IT must consider the following best practices:
- Have a written policy in place for employees that provides clear instructions and expectations around the usage of personal devices for work purposes.
- Require password protection for all devices and applications used to access company information to mitigate the risk of unauthorized access in case of loss or theft.
- Update the policy as technology and the threat landscape change.
- Detail what is acceptable use of BYOD devices and what is not.
- Adopt a zero-trust security model that limits user access to what is necessary for their job, requires authentications for all external connections and follows the principle of least privilege (POLP). This minimizes potential harm if an attacker breaches a user's device.
- Use device management tools such as MAM to ensure that corporate data is protected. Tools can also be used to enforce security policies such as remotely wiping data from lost or stolen devices.
- Encourage employees to keep their devices up to date with the latest versions of the operating system and software to minimize security vulnerabilities.
- Have a change management and monitoring strategy to ensure employees adhere to the policy.
- Have processes around addressing lost or stolen devices so employees can promptly report such incidents.
- Have processes around security incident response.
- Ensure that employees understand the dangers of connecting to unprotected Wi-Fi networks. Provide them with instructions on how to safeguard their devices and data, such as using VPNs when trying to access public networks.
- Train employees on BYOD during their onboarding. Also, provide regular security awareness training so employees can follow best practices and are aware of the risks involved with using their personal devices for work.
- Set clear expectations on what happens if an employee violates the policy.
Executing a BYOD policy
For organizations executing BYOD for the first time, one of the important aspects is setting expectations and training the employees. This should preferably be done during the registration process for the BYOD device or during an employee's HR and IT onboarding.
BYOD has proven to be an attractive policy for companies to adopt. It can bring convenience to employees along with cost savings for the company. Some in IT are concerned that personal devices pose a significant security risk, and without more controls of mobile devices, they are limited in the level of protection they can give. This concern has put some companies in the position of swapping out BYOD for corporate-owned devices.
A clearly articulated BYOD policy is essential for organizations permitting personal devices on their network. Learn the steps to develop and execute an effective BYOD policy.