
Getty Images
Mobile device management vs. mobile application management
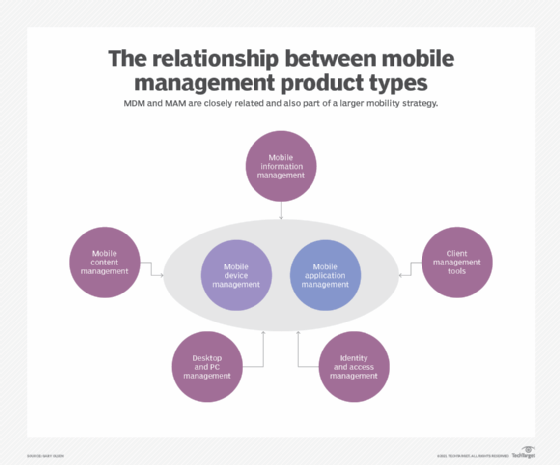
Mobile device management and mobile application management do different things but also overlap. Knowing their differences is important.
To help protect and control company data on mobile devices, IT leaders have turned to platforms that feature mobile device management and mobile application management tools.
MDM allows control over aspects of the device itself, such as the camera or passcodes. On the other hand, mobile application management (MAM) enables IT to manage app-specific security measures and limit what apps or data people can access.
Organizations generally employ both strategies, but it's important to know when and why an organization deploys one tool over the other.
Mobile device management vs. mobile application management
Managing a mobile device under an MDM deployment means that IT can control many aspects of the device regardless of its operating system. Some of the controls available using MDM include the following:
- enforcement of passcodes
- web filtering
- control of app deployments
- app and OS updates
- geofencing
- encryption of local storage
These controls are implemented through the MDM tool to ensure the device is used properly and reduce the risk of data leaks or breaches. For example, it can limit the device to only work activities by disabling access to social media or streaming sites.
Mobile application management, however, allows control over applications -- specifically corporate apps deployed on the device. Some of the following controls are available:
- require authentication or passcode for apps;
- disable copy/paste and screen capture on some mobile apps;
- mobile application sandboxing to separate it from other apps; and
- remote wipe of app data.
Implementing MDM on corporate devices is usually common practice as the organization owns the device and therefore requires full control. Alternatively, organizations with a BYOD policy may opt for a MAM-specific platform, as most employees will not feel comfortable giving their employer complete access to their personal devices.
Do organizations need both?
Generally speaking, MDM and MAM are complementary, not exclusionary. While organizations in the past might have had cause to choose between them, several enterprise mobility management and unified endpoint management platforms combine the capabilities of each into a single source.
Using a single platform to manage mobile devices drives efficiency across the organization, simplifying processes for IT and users alike. This single source enables a much more comprehensive and centralized view of all endpoints for an organization's perspective -- regardless of whether it is a mobile device, a server or a workstation.








