What is GSM (Global System for Mobile Communications)?
GSM (Global System for Mobile Communications) is a digital mobile communication standard applied widely in Europe and other parts of the world.
Globally compatible, GSM is more popular than another 2G mobile standard: code-division multiple access (CDMA), which is only available in a few countries. While CDMA is tied to a specific mobile phone and CDMA devices are locked to a specific carrier, GSM phones use subscriber identity module cards and can use different SIM cards from different carriers. Carrier switching -- not possible with CDMA - is easy with GSM because of its flexibility.
How GSM works
The evolution of wireless mobile telecommunications encompasses GSM, as well as High-Speed Circuit-Switched Data, General Packet Radio Service (GPRS), Enhanced Data rates for GSM Evolution (EDGE) and Universal Mobile Telecommunications Service (UMTS).
GSM uses a variation of time-division multiple access (TDMA) to subdivide a carrier frequency into different time slots. Typically, a 200 kilohertz radio channel is split into eight time slots. By separating the same bandwidth into multiple time slots, GSM enables multiple users -– typically eight to 16 -– to use that frequency for mobile communication.
In each time slot, information is transferred in bursts. GSM digitizes and compresses data and then sends it down a channel with two other streams of user data, each in its own time slot. Several components of the GSM system carry out these activities:
- Mobile station (MS). This is the cellphone that includes a SIM card, digital signal processor, radio transceiver and display. It initiates a call or data session.
- Base station subsystem (BSS). This consists of the base transceiver station (BTS) and the base station controller (BSC). The BTS receives a signal from the MS and forwards it to the BSC, which transfers the signal to the network switching subsystem.
- Network switching subsystem (NSS). The NSS handles call processing, call routing, flow management and connectivity. It includes a mobile switching centre (MSC) for call switching and forwarding; two databases -- visitor location register (VLR) and home location register (HLR) -- that store user information; equipment identity register, which is a list of functioning mobile devices; and authentication center, which verifies user identities and ensures privacy on every call. Once the MSC receives the signal from the BSC, it connects to the HLR and VLR to verify the user's identity and current location. It then routes the call to the intended recipient. If the user is roaming -- i.e., on a different network -- the MSC switches the call across networks. This facilitates seamless communication with minimal delays and without requiring users to change their devices or phone numbers.
GSM operates in a variety of frequency bands, with the 850 megahertz, 900 MHz, 1,800 MHz and 1,900 MHz frequency bands among the most common. The U.S. and other countries in North and South America usually use the 850 MHz/1,900 MHz band, while all other countries usually use the 900 MHz/1,800 MHz band.
Composition of the GSM network architecture
The GSM network has four separate parts that work together: the MS, BSS, NSS, and operation support system.
The mobile device connects to the network using hardware. The SIM card provides the network with identifying information about the mobile user.
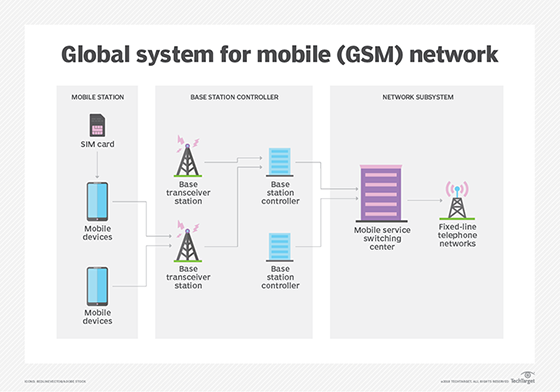
The BSS handles traffic between the cellphone and NSS. It consists of the BTS and BSC. The BTS contains the equipment that communicates with mobile phones, largely the radio transmitter receivers and antennas; the BSC is the intelligence behind it that communicates with and controls a group of BTSes.
The NSS, often called the core network, tracks the location of callers to enable cellular services delivery. Mobile carriers own the NSS. The NSS consists of numerous parts, including the MSC and HLR. These components perform different functions, such as routing calls and text messages and authenticating and storing caller account information using SIM cards.
Because many GSM network operators have roaming agreements with foreign operators, users can often continue to use their phones when they travel to other countries. SIM cards that hold home network access configurations can switch to those with metered local access, significantly reducing roaming costs with no reductions in service.
Benefits of GSM
For many years, GSM was the preferred technology for telecommunication ecosystems worldwide because of these benefits:
- Flexibility and convenience. Users can switch between phone carriers easily.
- Compatibility. Most carriers and phones used to be GSM-compatible, enabling users to connect and communicate seamlessly from any network and geographic location.
- Multiple uses. Users on a GSM network could browse the internet, check emails, watch streaming videos and connect with others through social networking sites -- all from the same device.
- Roaming support. Users could use the same device and number even while traveling outside their home network.
What are some limitations of GSM?
Here are some disadvantages of GSM:
- Electronic interference. Because GSM uses a pulse-transmission technology, it is known to interfere with electronics, like hearing aids. This electromagnetic interference is why certain places like airports, gas stations and hospitals require that mobile phones be turned off.
- Bandwidth lag. When using GSM technologies, multiple users access the same bandwidth, sometimes resulting in considerable latency as more users join the network.
- Limited rate of data transfer. GSM offers a somewhat limited data transfer rate. To achieve higher data rates, a user must switch to a device with more advanced forms of GSM.
- Repeaters. GSM requires carriers to install repeaters to increase coverage.
GSM security controls and security concerns
GSM was designed as a secure wireless system with security features to protect user data, ensure user privacy and safeguard communications from unauthorized access and eavesdropping. For example, it uses authentication measures, such as challenge-response authentication, which prompts a user to provide a valid answer to a question, and a preshared key in the form of a password or passphrase. GSM also employs cryptographic security algorithms, including stream ciphers, like A5/1, A5/2 and A5/3, that encrypt plaintext digits and ensure the privacy of user conversations.
Despite having these features, GSM does not offer impenetrable security; it is susceptible to attacks. For example, the algorithms for both A5/1 and A5/2 have been broken and published in the past. Furthermore, GPRS Encryption Algorithm 1 and GEA2 -- ciphers in GPRS, a packet-based communication service that GSM uses to transmit data -- have also been broken and published. Open source software is also available to sniff packets in the GPRS network easily. Given these vulnerabilities, GSM is vulnerable to plaintext attacks, which can compromise communications and user data.
History of GSM
The GSM standard debuted in the early 1980s when it was originally known as Groupe Spécial Mobile. However, it wasn't until the early 1990s when it was first implemented in Europe. The goal was to provide a unified mobile communication standard for all of Europe.
The GSM standard was meant to eliminate compatibility issues common with pre-GSM analog telecommunications systems, such as Advanced Mobile Phone System (AMPS) in the U.S. and Total Access Communication System in the U.K. These GSM predecessors were also unable to scale with the adoption of more users. The shortcomings of these systems signaled the need for more efficient cellular technology suitable for international use.
The European Conference of Postal and Telecommunications Administrations (CEPT) in 1983 worked to develop a European standard for digital telecommunications. CEPT listed several criteria the new system must meet: international roaming support, high speech quality, support for handheld devices, low service cost, flexibility to accommodate new services and Integrated Services Digital Network capability.
In 1987, representatives from 13 European countries signed a contract to deploy a telecommunications standard. The European Union (EU) then passed laws to require GSM as a standard in Europe. In 1989, the responsibility of the GSM project was transferred from CEPT to the European Telecommunications Standards Institute.
Mobile services based on GSM were finally launched in Finland in 1991. That same year, the GSM standard frequency band was expanded from 900 MHz to 1,800 MHz. By 2010, GSM represented 80% of the global mobile market.
Since then, GSM use has declined, and GSM is becoming increasingly obsolete, particularly as more mobile phones are switching to newer technologies, like 5G. Several telecommunications carriers, such as AT&T, Cellcom and Verizon in the U.S. and Telstra in Australia, have decommissioned their GSM networks. In 2017, Singapore retired its 2G GSM network. Some other U.S. carriers, such as T-Mobile, have also announced plans to switch off 2G.
GSM vs. CDMA vs. LTE: Differences
GSM, CDMA and Long-Term Evolution (LTE) cellular-wireless communications use different technologies and are meant to meet different business objectives. GSM is the oldest; it initially relied on processor/chip technologies available at the time to encode and decode data.
For a time, mobile operators deployed 2G GSM across many countries worldwide except for the U.S. and several countries in South America. Incompatibility with existing analog AMPS services largely drove these exceptions. To provide the necessary interim compatibility with GSM, they evaluated GSM's economies of scale for their networks.
Carriers employed Digital AMPS, based on Interim Standard (IS)-136 for TDMA networking from the Electronics Industries Association/Telecommunication Industry Association. TDMA protocols were not sufficiently spectrum-efficient to support fast-growing cellular services, leading to the introduction of the CDMA protocol.
Also known as ITU IS-95, cdmaOne became the CDMA digital cellular standard in 1993, gaining popularity in countries using older analog AMPS. However, cdmaOne needed powerful processors to provide the additional compute power needed for coding and decoding CDMA. This is why CDMA phones were more expensive than GSM models.
GSM introduced GPRS for data in 2000, which then led to EDGE, while cdmaOne led to American National Standards Institute-2000 1xRTT and then to Evolution-Data Optimized. Because CDMA protocols provide superior spectrum efficiency, 3rd Generation Partnership Project adopted these protocols under Wideband CDMA for implementation in 3G UMTS.
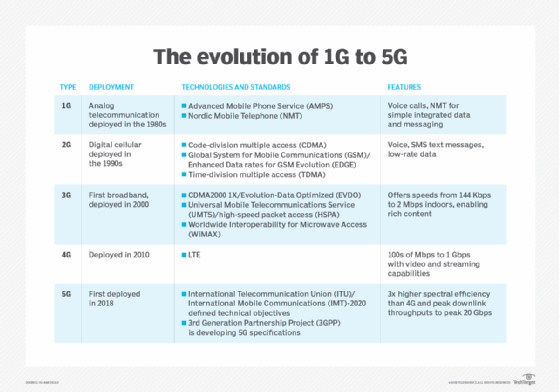
4G LTE is a GSM technology and a major upgrade over 3G in data transfer speeds. It doesn't offer any way to make regular phone calls in the traditional sense. Instead, it uses specialized voice over Internet Protocol for what's referred to as voice over LTE.
CDMA and GSM technologies eventually converged through orthogonal frequency-division multiple access (OFDMA), LTE's encoding protocol. OFDMA is also the encoding protocol for Worldwide Interoperability for Microwave Access and Wi-Fi networks.
GSM or CDMA: Which is more popular?
Between GSM and CDMA, GSM -- and, by extension, its descendants, 5G New Radio, UMTS and LTE -- is more popular. For almost three decades, GSM-based technologies were deployed in practically every country in the world. In the U.S., most carriers used GSM to provide mobile services.
CDMA was always used in fewer countries compared to GSM. Also, more carriers that use CDMA are shutting down or phasing out their CDMA networks. But this now applies to GSM also.
As 5G becomes more commonplace, it is expected to come with new encoding protocols. Many telecommunications industry watchers predict it will have a global and dramatic effect on digital communications.
Most carriers are asking their customers to switch over to 4G and, if possible, to 5G-ready devices if they haven't already. Some, like T-Mobile, are also offering free replacements for older handsets.
Wireless networking improves from generation to generation. Learn more about the basics behind 5G.






